To remove Backdoor.Subseven you need to do the following:
· Run Update to make sure that you have the most recent definitions.
· Run a full system scan, making sure that antivirus software is set to scan all files.
· Make a copy of the Regedit.exe file with the .com extension (if necessary).
· Remove the references added to the Win.ini and System.ini files.
· Remove the references added to the Windows registry.
For detailed instructions, see the sections that follow.
NOTES:
· This is a random-name file creator. We will use the example Eutccec.exe in this document. Please substitute the randomly named file that you find on the system.
To run Update and then scan with AV software
Run Update, and then run a full system scan. Make sure that Antivirus is set to scan all files.
NOTE: If you cannot do this because you cannot run program files, go first to the section titled To copy Regedit.exe to Regedit.com; otherwise, skip to the section titled To edit the registry.
To copy Regedit.exe to Regedit.com:
If you cannot run program files, then you must copy Regedit.exe to Regedit.com; otherwise, skip to the next section.
1. Do one of the following, depending on which operating system you are running:
o Windows NT/2000/XP
1. Click Start, and click Run.
2. Click Browse, and then browse to the \Winnt\system32 folder.
3. Double-click the Command.com file, and then click OK.
1. Type copy regedit.exe regedit.com and then press Enter.
2. Type start regedit.com and then press Enter.
3. Proceed to To edit the registry.
NOTES:
· The Registry Editor will open in front of the DOS window. After you finish editing the registry and have closed the Registry Editor, then close the DOS window, as well.
· After BackDoor.Subseven has been successfully removed, then you may delete the Regedit.com file.
To edit the registry
CAUTION: It is strongly recommend that you back up the system registry before making any changes. Incorrect changes to the registry can result in permanent data loss or corrupted files. Please make sure you modify only the keys specified in this document.
1. Start the Registry Editor if necessary:
o If you performed the procedures in the previous section, then the Registry Editor is already open. Skip to step 4.
o If it was not necessary to perform the procedures in the previous section, then proceed to step 2.
2. Click Start, and click Run. The Run dialog box appears.
3. Type regedit and then click OK. The Registry Editor opens.
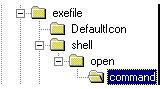
4. Navigate to and open the following key:
HKEY_LOCAL_MACHINE\Software\Classes\exefile\shell\open\command
CAUTION: Do not inadvertently modify the HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.exe subkey. Changes made to that key can prevent .exe files (program files) from running. Be sure to navigate to the HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command subkey as shown in the following figure.
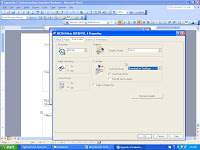
5. Double-click the (Default) value in the right pane.
6. Delete the current value data, and then type: "%1" %* (quote-percent-one-quote-space-percent-asterisk.)
NOTE: The Registry Editor will automatically enclose the value within quotation marks. When you click OK, the (Default) value should look exactly like this: ""%1" %*"
Make sure that you completely delete all value data in the command key prior to typing the correct data. If you accidentally leave a space at the beginning of the entry, any attempt to run program files will result in the error message "Windows cannot find .exe." If this happens to you, then start over at the beginning of this document, making sure to completely remove the current value data.
7. Navigate to and select the following key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
8. In the right pane, look under the Name column, and delete any of the following values if you see them:
WINLOADER, Win32nt, Win32.Bin, WinCrypt, WinProtect, Win, xTnow, Ayespie,
PowerSaveMonitor, rundll32
NOTE:Other values may appear, which are not on this list. Deleting values from this location does not prevent the programs from running; it only prevents them from starting automatically when Windows starts.
9. Navigate to and select the following key:
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\RunServices
10. In the right pane, look under the Name column, and delete any of the following values if you see them:
WINLOADER
Win32nt
Win32.Bin
WinProtect
Win
xTnow
Ayespie
PowerSaveMonitor
rundll32
NOTE: Other values may appear, which are not on this list. Deleting values from this location does not prevent the programs from running; it only prevents them from starting automatically when Windows starts.
11. Exit the Registry Editor.
Edit Windows startup files
1. Click Start, and click Run.
2. Type the following command, and then press Enter to open the System Configuration Editor.
sysedit
NOTE: If you see the message "Windows cannot find .exe", then repeat steps 1 through 6 in the previous section, and make sure that you typed the text exactly as shown. If you do not see an error message, then proceed to the next step.
3. Close the Autoexec.bat and Config.sys windows in the System Configuration Editor.
CAUTION: The steps that follow instruct you to remove text from the load= and run= lines of the Win.ini file. If you are using older programs, they may be loading at startup from one of these lines. The Trojan adds lines such as load=c:\windows\temp\pkg2350.exe or run=hpfsched
msrexe.exe. (In this example, hpfsched is a legitimate program, but msrexe.exe is part of the Trojan). It may also modify the shell= statement, for example, to shell=explorer.exe pwrsvm.exe
If you are sure that the text contained in these lines are for programs that you normally use, then we suggest that you do not remove them. If you are not sure, but the text does not refer to the file names shown, then you can prevent the lines from loading by placing a semicolon in the first character position of the line. For example:
; run=accounts.exe
4. Locate the load= line within the [windows] section of the Win.ini file; it is usually located near the top of the file.
5. Position the cursor immediately to the right of the equal (=) sign.
6. Press Shift+End to select all of the text to the right of the equal sign, and then press Delete.
7. Repeat steps 4 to 6 for the run= line, which is usually beneath the load= line.
8. Close the Win.ini window, and click Yes when you are prompted whether to save the changes.
9. Locate the shell=explorer.exe line within the [boot] section of the System.ini file; it is usually located near the top of the file.
10. Position the cursor immediately to the right of explorer.exe.
11. Press Shift+End to select all of the text to the right of explorer.exe and then press Delete.
12. Close the System.ini window, and click Yes when you are prompted whether to save the changes.
NOTE: Some computers may have an entry other than explorer.exe after shell=. If this is the case, and you are running an alternate Windows shell, then change this line to shell=explorer.exe for now. You can change it back to your alternate shell after you have finished this procedure.
13. Exit the System Configuration Editor.
14. Click Start, point to Settings, and click Control Panel.
15. Double-click the Display icon.
16. Click the Screen Saver tab, and then change the currently selected screen saver. If it is set to (None), then select any of the available screen savers. The important thing is that you make a change to the current setting.
17. Click OK, and then close the Control Panel.
This completes the removal part of the process. Even if you did so previously, start antivirus and run a full system scan. Delete any files found to be infected with Backdoor.Subseven. When finished, restart the computer.

 Fig.2
Fig.2 Fig.3
Fig.3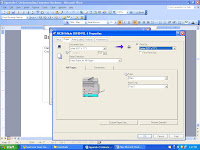 Fig.4
Fig.4